Rethinking Compliance as a Strategic Advantage in 2025
When it comes to cybersecurity and compliance, many organizations still fall into the same trap: they chase certifications like SOC ...
Tech News
Artificial Intelligence
The AI Takeover: Is ChatGPT the New Office and Photoshop?
Artificial Intelligence
The Unclaimed Identity: Why Autonomous AI Agents Are the Next Governance Crisis
Artificial Intelligence
How a Psychology Background Makes for Better AI Adoption
Latest on TechSpective
Blog
Energy as the Engine: Driving Economic Policy in Emerging Nations
In the intricate dance of global economics, energy has always played a pivotal role. For emerging nations, however, it’s not ...
Rob Enderle
July 25, 2025
Blog
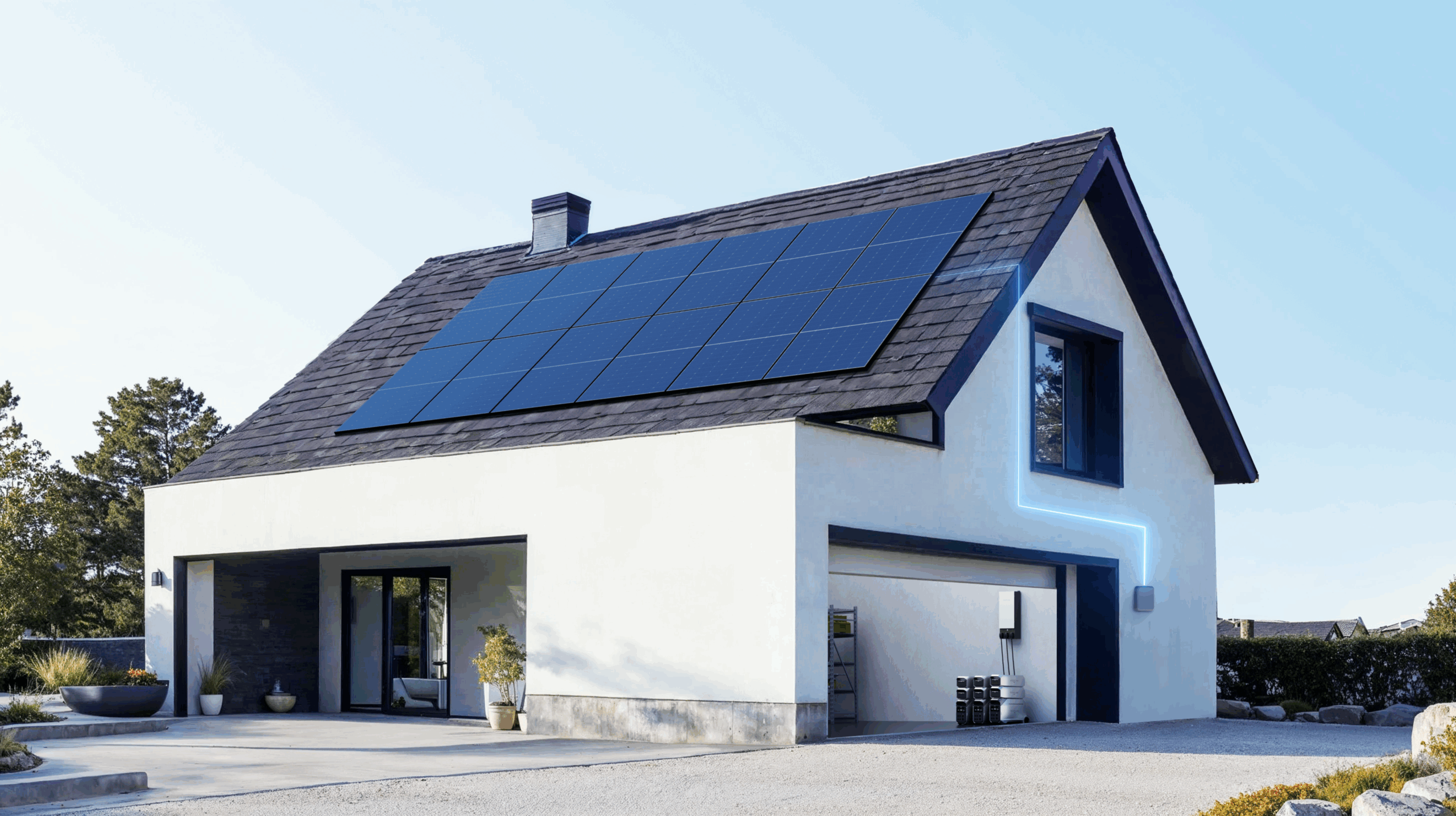
Review: EcoFlow DELTA Pro 3 Portable Power Station
When it comes to backup power, most people have to choose between portability and performance. The EcoFlow DELTA Pro 3 ...
Tony Bradley
July 21, 2025
Blog
Review: EcoFlow Smart Home Panel 2
Power outages aren’t just inconvenient—they’re increasingly common. Whether it’s rolling blackouts, summer storms, or aging grid infrastructure, more homeowners are ...
Tony Bradley
July 21, 2025
Blog
Future-Proofing Your Data Infrastructure with Post-Quantum Cryptography
The arrival of quantum computing isn’t a question of if—but when. And when it does arrive at scale, it will ...
Gagan Gulati
July 21, 2025
Blog
Navigating Cybersecurity Complexity
The ever-expanding world of cybersecurity is full of big promises, bold claims, and—if we’re being honest—a lot of noise. As ...
Tony Bradley
July 18, 2025
Security
Navigating Cybersecurity Complexity
Tony Bradley
July 18, 2025
The ever-expanding world of cybersecurity is full of big promises, bold claims, ...
The Unclaimed Identity: Why Autonomous AI Agents Are the Next Governance Crisis
Rosario Mastrogiacomo
July 17, 2025
As enterprises scale their use of artificial intelligence, a hidden governance crisis ...
AI Voice Clones and Mobile Phishing: The Cyber Threats You’re Not Ready For
Tony Bradley
July 11, 2025
Cybercriminals are evolving—and they’ve set their sights on your smartphone. For years, ...